
A powerful, easily deployable network traffic analysis tool suite for network security monitoring
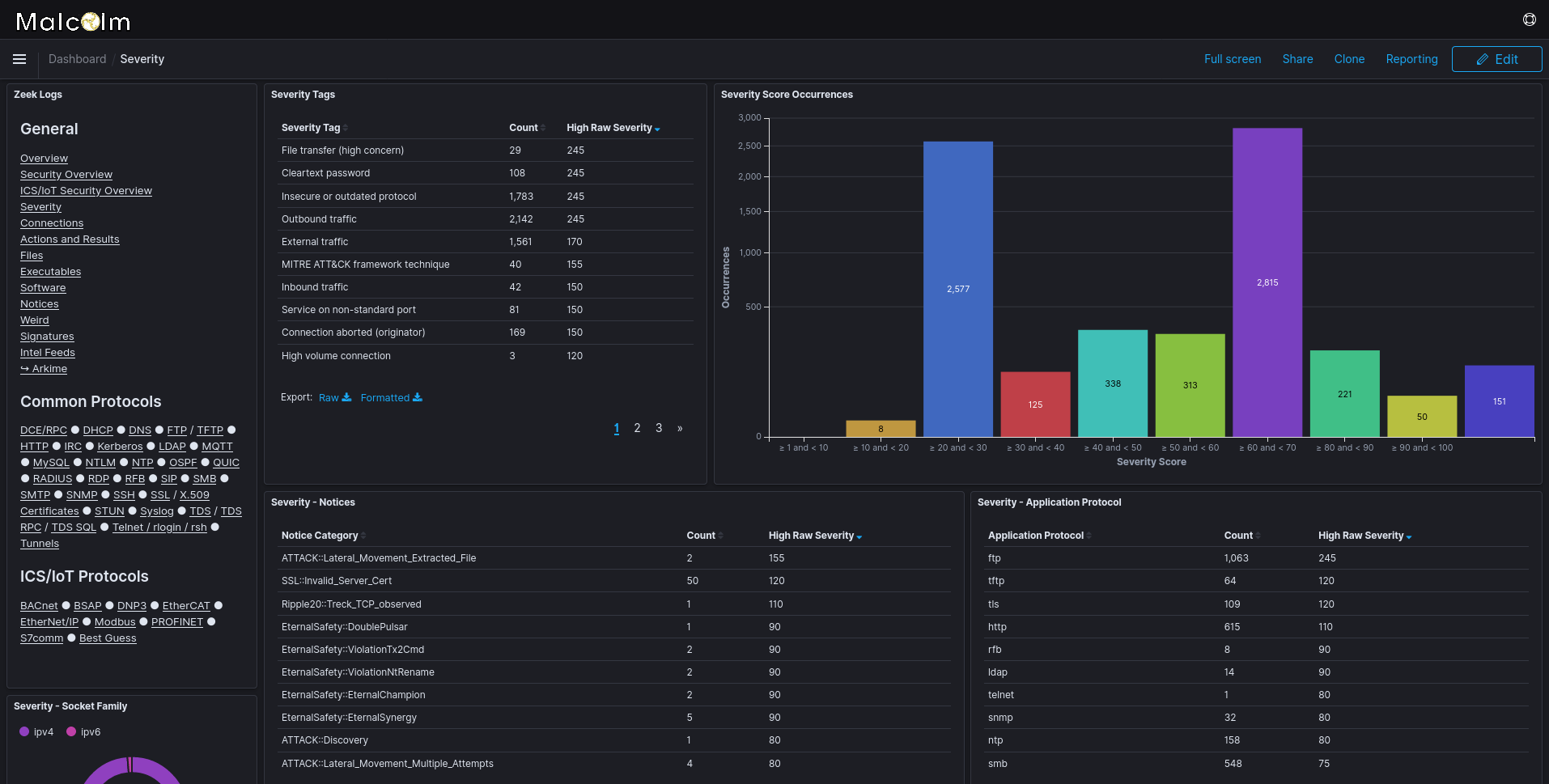
Event severity scoring
As Zeek logs are parsed and enriched prior to indexing, a severity score up to 100 (a higher score indicating a more severe event) can be assigned when one or more of the following conditions are met:
- cross-segment network traffic (if network subnets were defined)
- connection origination and destination (e.g., inbound, outbound, external, internal)
- traffic to or from sensitive countries
- The comma-separated list of countries (by ISO 3166-1 alpha-2 code) can be customized by setting the
SENSITIVE_COUNTRY_CODESenvironment variable inlookup-common.env
- The comma-separated list of countries (by ISO 3166-1 alpha-2 code) can be customized by setting the
- domain names (from DNS queries and SSL server names) with high entropy as calculated by freq
- The entropy threshold for this condition to trigger can be adjusted by setting the
FREQ_SEVERITY_THRESHOLDenvironment variable inlookup-common.env. A lower value will only assign severity scores to fewer domain names with higher entropy (e.g.,2.0forNQZHTFHRMYMTVBQJE.COM), while a higher value will assign severity scores to more domain names with lower entropy (e.g.,7.5fornaturallanguagedomain.example.org)
- The entropy threshold for this condition to trigger can be adjusted by setting the
- file transfers (categorized by mime type)
notice.log,intel.logandweird.logentries, including those generated by Zeek plugins detecting vulnerabilities (see the list of Zeek plugins under Components)- detection of cleartext passwords
- use of insecure or outdated protocols
- tunneled traffic or use of VPN protocols
- rejected or aborted connections
- common network services communicating over non-standard ports
- file scanning engine hits on extracted files
- large connection or file transfer
- The size (in megabytes) threshold for this condition to trigger can be adjusted by setting the
TOTAL_MEGABYTES_SEVERITY_THRESHOLDenvironment variable inlookup-common.env
- The size (in megabytes) threshold for this condition to trigger can be adjusted by setting the
- long connection duration
- Long connections are determined by the zeek-long-connections plugin. See the corresponding environment variables in
zeek.envfor tuning.
- Long connections are determined by the zeek-long-connections plugin. See the corresponding environment variables in
As this feature is improved, it is expected additional severity scoring categories will be identified and implemented.
When a Zeek log satisfies more than one of these conditions its severity scores will be summed, with a maximum score of 100. A Zeek log’s severity score is indexed in the event.severity field and the conditions that contributed to its score are indexed in event.severity_tags.
Customizing event severity scoring
The category severity scores can be customized by editing logstash/maps/malcolm_severity.yaml:
- Each category can be assigned a number between
1and100for severity scoring. - Any category may be disabled by assigning it a score of
0. - A severity score can be assigned for any supported protocol by adding an entry with the key formatted like
"PROTOCOL_XYZ", whereXYZis the uppercased value of the protocol as stored in thenetwork.protocolfield. For example, to assign a score of40to Zeek logs generated for SSH traffic, you could add the following line tomalcolm_severity.yaml:
"PROTOCOL_SSH": 40
Restart Logstash after modifying malcolm_severity.yaml for the changes to take effect.
Severity scoring can be disabled globally by setting the LOGSTASH_SEVERITY_SCORING environment variable to false in the logstash.env file and restarting Malcolm.